CloudFormation Hooks for infra compliance checks
Context
AWS CloudFormation team has made “Hooks” generally available through the CloudFormation public extensions. So what are these hooks you speak of ?
From the docs :
Hooks proactively inspect the configuration of your AWS resources before provisioning. If non-compliant resources are found, AWS CloudFormation returns a failure status and either fails the operation or provides a warning and allows the operation to continue based on the hook failure mode. You can use pre-built hooks or build your own hooks using the CloudFormation Command Line Interface (CloudFormation CLI).
Why does it matter ?
The key point here is “proactive & automated validation” of infrastructure stacks deployed via CloudFormation api which is one area of concern for security and infrastructure engineers having oversight into the accounts which application teams have access to deploy to. Solutions like checkov, cfn_nag, regula do provide some reprieve in this matter supporting some of the commonly known security vulnerabilities. Hooks seem to have caught up to this finally. The ability to enforce these on an organization level using internal registries should come as a welcome note to security & most teams managing the day to day operations of these accounts.
Few things to keep in mind :
- Hook : Your code which does all the dirty work. They can review the CloudFormation stack against the logic defined by you to mark them as failed ( or issue a warning if thats the case)
- Hook Targets : What you are targeting with the code in the hook. “AWS::S3::Bucket” for example
- Target Invocation Point : When do you want to run this ? “PRE” seems the current option available and suits my usecase for compliance checks.
- Target Action : What CloudFormation trigger should this hook be executed against . common ones being CREATE or UPDATE
Usecase
- Enforce encryption on S3 buckets as a pre-check.
The hook I am going to use is available in the AWS Samples repository under the python-hooks called “s3-bucket-encryption”
What does it take to enable the hook ?
From AWS Clouformation console, these can be accessed/activated from the public extensions on the registry.In this case I am selecting the S3 encryption hook from the aws samples hooks library
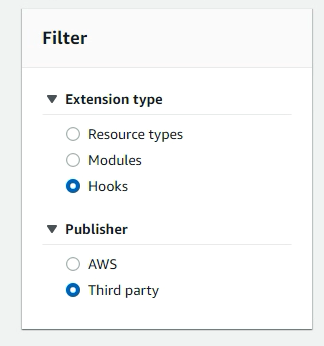
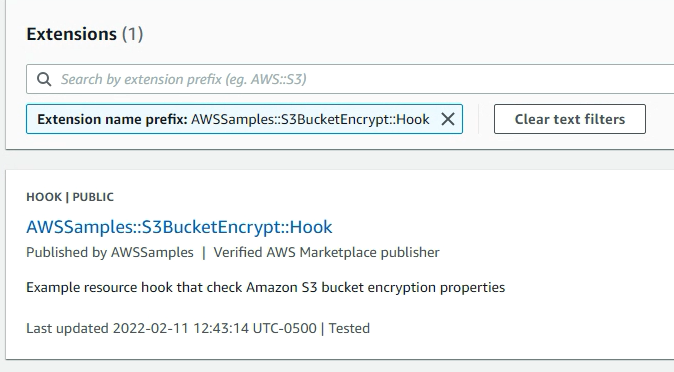
Activating a hook via the console involves:
- Selecting “Activate” after finding the desired hook
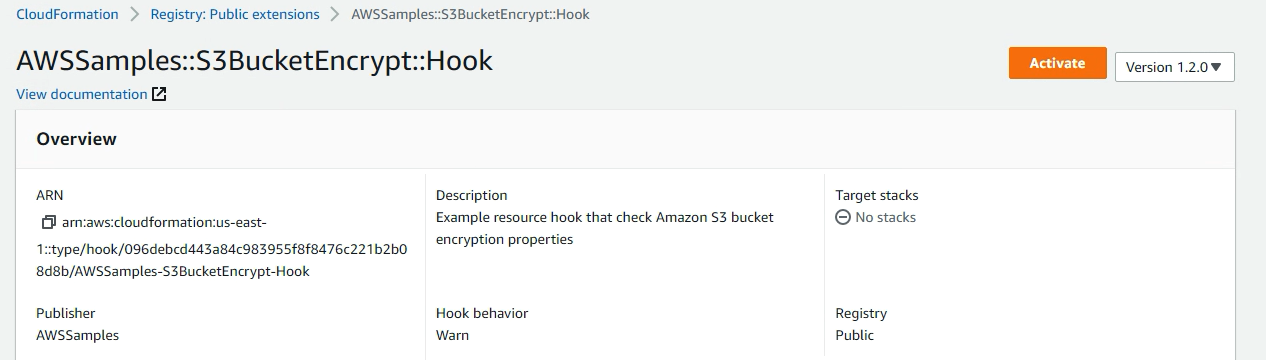
- Specifying an execution role which is already provided in the reference blog below.
- Selecting Configure now and setting a configuration from your side. Configuration settings dictate what you want to do when the checks pass or fail. An example below
{
"CloudFormationConfiguration": {
"HookConfiguration": {
"TargetStacks": "ALL",
"FailureMode": "FAIL",
"Properties": {
"minBuckets": "1",
"encryptionAlgorithm": "aws:kms"
}
}
}
}
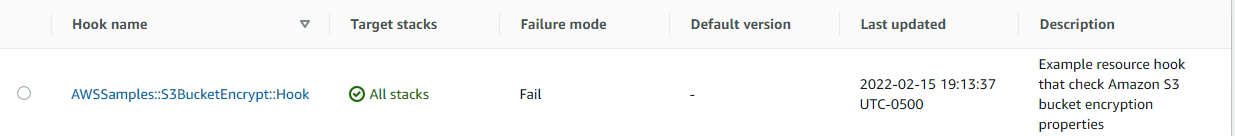
The hook should be activated and available under the activated hooks list as below.
Testing with a CDK stack
Considering AWS CDK code I use synthesizes into ClouFormation, this is a no brainer to add to further codify the infrastructure deployment process.
- Snippet of the CDK code in python which deploys an S3 with all the defaults per documentation. Note that the bucket is in an unencrypted state in this stack.
from aws_cdk.core import Stack, Construct
from aws_cdk.aws_s3 import Bucket
class HooksStack(Stack):
def __init__(self, scope: Construct, construct_id: str, **kwargs) -> None:
super().__init__(scope, construct_id, **kwargs)
Bucket(self, "test-cdk-hooks", bucket_name="test-cdk-hooks")
Deploying the cdk stack gives you
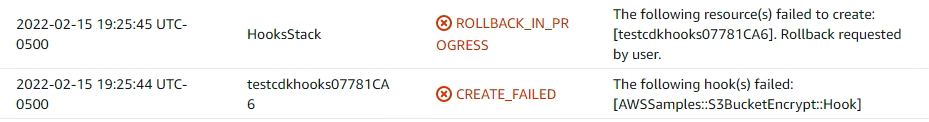
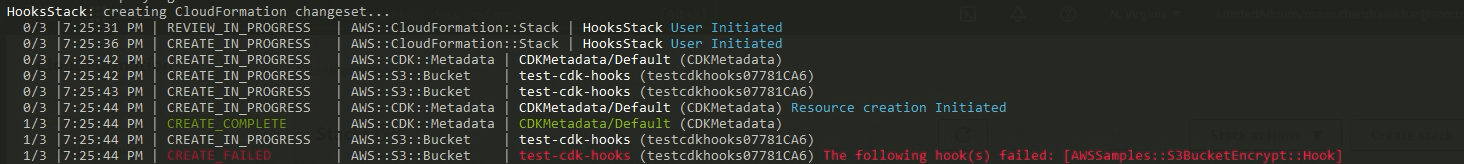 Following the cloudformaiton api response for a create_failed, the stack goes into a rollback mode preserving the previous state.
Following the cloudformaiton api response for a create_failed, the stack goes into a rollback mode preserving the previous state.
Conclusion
- This does seem like a step in the right direction from the infrastucture standpoint where compliance and security teams can spend less time on remediating these issues and more on specifying the controls which can codified and then enforced.
- I have only talked about setting this via the console and the options to activate public extensions do exist with the cli and boto3 as well.
Appendix
- Reference blog : https://aws.amazon.com/blogs/mt/proactively-keep-resources-secure-and-compliant-with-aws-cloudformation-hooks/
- Reference sample hook : https://github.com/aws-cloudformation/aws-cloudformation-samples/tree/main/hooks/python-hooks/s3-bucket-encryption
- Hooks structure : https://docs.aws.amazon.com/cloudformation-cli/latest/userguide/hooks-structure.html
- Boto3 reference : https://boto3.amazonaws.com/v1/documentation/api/latest/reference/services/cloudformation.html#CloudFormation.Client.activate_type