Secure your CDK code from misconfigurations
Context
IAC or infrastructure as Code is one of the practices which most clients of mine have started picking up along with CICD pipelines. In short, an IAC library or tools helps you to model infrastructure as code or some easy to use configuration language (HCL for example). Tools like AWS Cloudformation, Azure RM templates were probably the first steps from the Cloud providers to provide their customers with something similar.
Problem Statement
So you as a developer have started including a configuration/code to provision infrastructure to support your application.
- Are you doing it right ?
- Are you creating secure infrastructure ?
These questions have led both the developer community and organizations they belong to take a guarded approach in allowing the developers take ownership of provisioning infrastructure themselves. Yes, you do have some DevOps consultants who are brought into support these engagements to enable the developers to do the right thing. Wouldn’t it be a good option to have a tool to actually verify your IAC code before you deploy them to the cloud provider you use ? The main intent of these tools or libraries would be review your IAC templates against possible misconfigurations which can cause a heartburn later.
What is cdk-nag
cdk-nag is one such tool which reviews your templates for common patterns which would lead to insecure infrastructure. This project is inspired by the Cloudformation variant called cfn-nag which lists some of the below rulesets among many.
- IAM rules that are too permissive (wildcards)
- Security group rules that are too permissive (wildcards)
- Access logs that aren’t enabled
- Encryption that isn’t enabled
- Password literals
Usage
The usage of cdk-nag is very simple as it can be added on to the Aspects in a stack which is calling a construct you have created.
- Import the cdk-nag package in your requirements.txt
- Import the AwsSolutionsChecks from the cdk_ng module in the app Stack which is using the construct
- Perform cdk synth
Below is a python example for the same.
Sample python Construct
1from aws_cdk import Duration, Stack, aws_sqs as sqs,
2from constructs import Construct
3
4class CdkNagTestStack(Stack):
5
6 def __init__(self, scope: Construct, construct_id: str, **kwargs) -> None:
7 super().__init__(scope, construct_id, **kwargs)
8 queue = sqs.Queue(
9 self, "CdkNagTestQueue",
10 visibility_timeout=Duration.seconds(300),
11 )
The stack referencing the construct with the Aspects.
1#!/usr/bin/env python3
2import os
3
4import aws_cdk as cdk
5from aws_cdk import Aspects
6from cdk_nag import AwsSolutionsChecks
7from cdk_nag_test.cdk_nag_test_stack import CdkNagTestStack
8
9app = cdk.App()
10CdkNagTestStack(app, "CdkNagTestStack")
11Aspects.of(app).add(AwsSolutionsChecks())
12app.synth()
For the simple queue that is in the stack above, cdk-nag gives me :
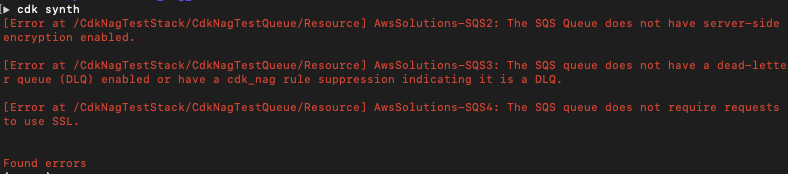
If you wanted to have verbose logs on it, you can adjust the Aspects with a flag. The rules are currently in here
As the documentation states, AwsSolutionsChecks is just of the rule packs present on the library and you can add the additional ones like below as well.
Conclusion:
- If you are using aws cdk for infrastructure provisioning , this is a no brainer to use.
- The library allows you to create your NagPacks for conformance you need in addition to the ones listed.
- Exclusion of rules was something which I couldn’t use with checkov which I was using it which made a list of false positives which my devs stopped looking at.
- Suppressions of rules is something which cdk-nag supports, although it is for a smaller subset.